
About Me
Beginning at a young age, I found myself enthralled with computers. Early on, using Windows XP on a little tablet PC, I would look up “how to make a virus” on YouTube, thus leading to my start into basic programming using VBScript. This wasn’t anything serious, just a basic file that when ran, displayed a fake messagebox and would shut down your machine. Kinda like the following
@echo off
x=msgbox("I eated all your cookies and deleted System32. Goodbye" ,0, "YoUvE bEeN hAcKeD")
shutdown /t 1 /sFrom there, I would use this and memorize a bit of it so I could run it on my babysitters laptop (where I would also find my first introduction to Linux through Ubuntu), the school machines, and more.
Through middle school, I continued my learning of computers among other things, taking up baseball and excelling in Robotics. By the end of my first Robotics course, I was already ahead another course. Here in the states, we commonly have i.e. Robotics 1A and Robotics 2A, then 1B, 2B, and so forth. With quarters and depending on school schedule, 2A/B would be the second year of Robotics. My memory is fuzzy in regards to this but you get the example. Our final for the A series was to complete a basic traffic light that’s timed and has an “emergency red” button for an example situation to simulate a firetruck or EMT coming through. This was all done on Vexnet Robotics, which while expensive, were fun as hell and easy to do. My final ended up being to create a robotic RC car using the controllers that the Robotic team would usually do for their more advanced items.
That was my more ethical side of things for computers. When I was bored or before class started in some classes, I would log onto our Windows 7 machines. I poked around, looking through what I could and couldn’t. And during this time, our district had all schools and misc. branches networked together without any restriction policy (at least that I could see). This meant that for a decently large district, I could see about 1k of computers connected to the network (if I recall correctly). This wasn’t like an NMap scan, but rather through the network discovery in Windows Explorer. Every machine, every server, every endpoint that a Windows desktop could see. Right there in my hands.
Now this wasn’t the best part – our credentials were viable for every machine we logged onto. We used an Active Directory system (with a special script that I’ll get into shortly) that allowed us to login wherever we needed. So if you had class for Typing 1 (stuff like using word, MS Paint, etc.), you could log on in that classroom and then next period, log into the art machines to pull up references for example. That and our “U” drives. Referencing the drive letter that was assigned as our personal file storage. None of the machines would keep your data but keeping items in your U drive would allow you to take them with you. That was before we had a full GSuite account and all (and the Great Chromebook Revolution and all, ykno.).
Now the script…the script was a login script. Ran each time any student signed on that was a part of the domain. For some odd reason, the two domain controllers were viewable through that network tab. The even stranger thing – I could view many of the files and items that were a part of the domain controller. Nothing too serious, mostly items that I could probably read as it is, but they made the whole directory where the script was stored not only viewable – but writable. This is where my devious plan to replace this “logon.bat” script with my own. I replaced all the text in that file with one I quickly found, the old but gold “eject and reinsert your CD drive until you go insane”. Thinking this would never work – I hit save and off to the races….
The warning bell rang, and everyone went to their seats. Mind you, this was the typing class I was in where I just made all those changes. So you can imagine my amazement and shock to hear not one, not two, but 30 something machines (including our teacher, who I believe was Mr. Z) all of a sudden either ejecting and inserting their drives, or buzzing in an attempt to spit out the tray after so many years of abuse by kids.
By the end of the day, I had a few friends asking me about it and if I did it. Probably the best high of my life, right next to stealing the backup Microsoft Access database for all student IDs and passwords (not hard, since its our birthdate which was stored in that same DB). That one I didn’t use much outside of signing into the EAP wifi so if I did something on the internet I wasn’t supposed to – it wasn’t my problem.
Much of this knowledge has only grown over the years, helping me pursue my knowledge of Linux, working on Windows Server 2012, and so much more. With CyberPatriot in my high school, it only helped to fuel the fire of passion about technology in my heart. It was aggravating each year making it to semi-finals and losing to the same California Boeing-sponsored school every year, but I think many of these memories are what make me who I am today.
As you watch my content and read my articles, I hope that I can help spark and ignite that same passion in your heart as I did with myself. To gain the knowledge and understanding on how to retain your privacy, increase your system security, and understand more of the electronic world around us. Don’t think that you need any sort of degree or certification in order to know this stuff. It helps, yes, but you can always be the pioneer in your knowledge and career. The certification/diploma just tells someone you know what you’re talking about and a trusted third party can vouch for it.
Certifications


Growth-Driven Design
Completion of the GDD/Growth-Driven Design framework course by Hubspot


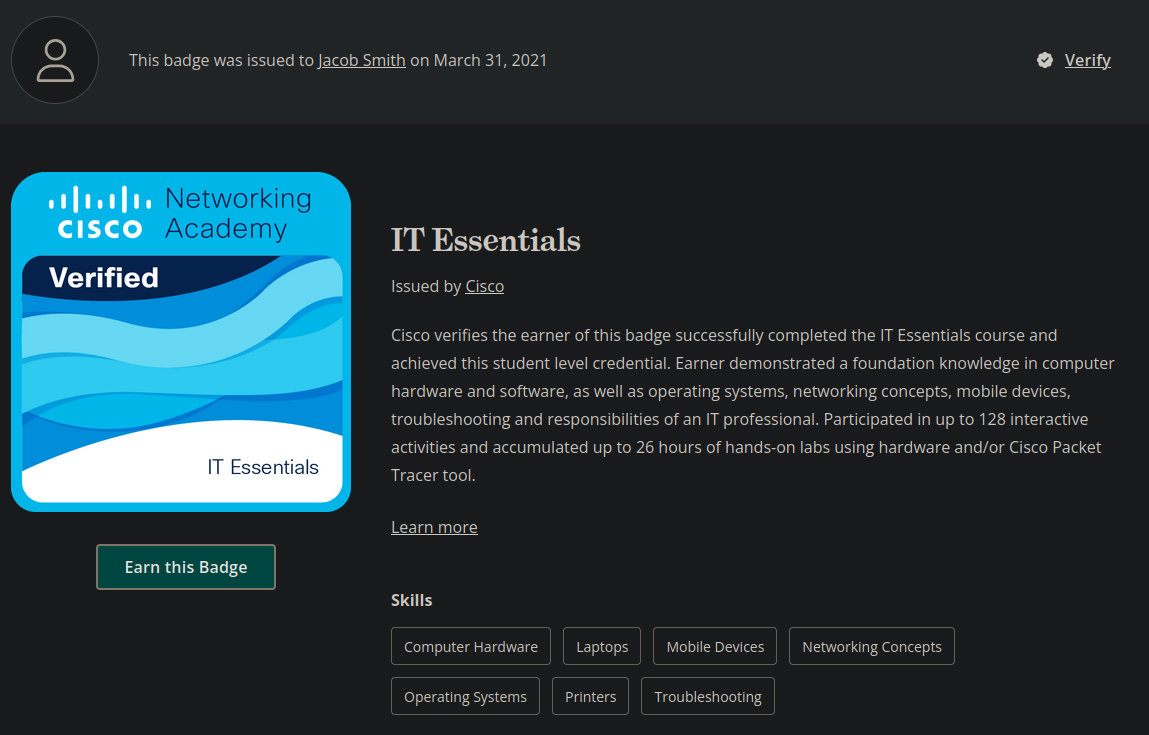
CISCO IT Essentials
Represents a foundation knowledge in OSes, networking, troubleshooting, and more.
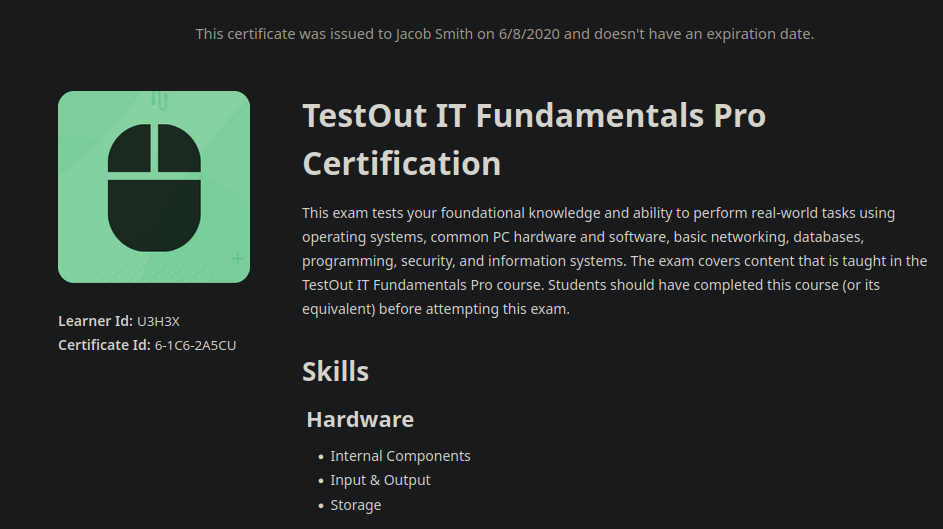
TestOut IT Fundamentals Pro
Similar to Cisco IT Essentials, a now deprecated cert. from TestOut (now a part of CompTIA)
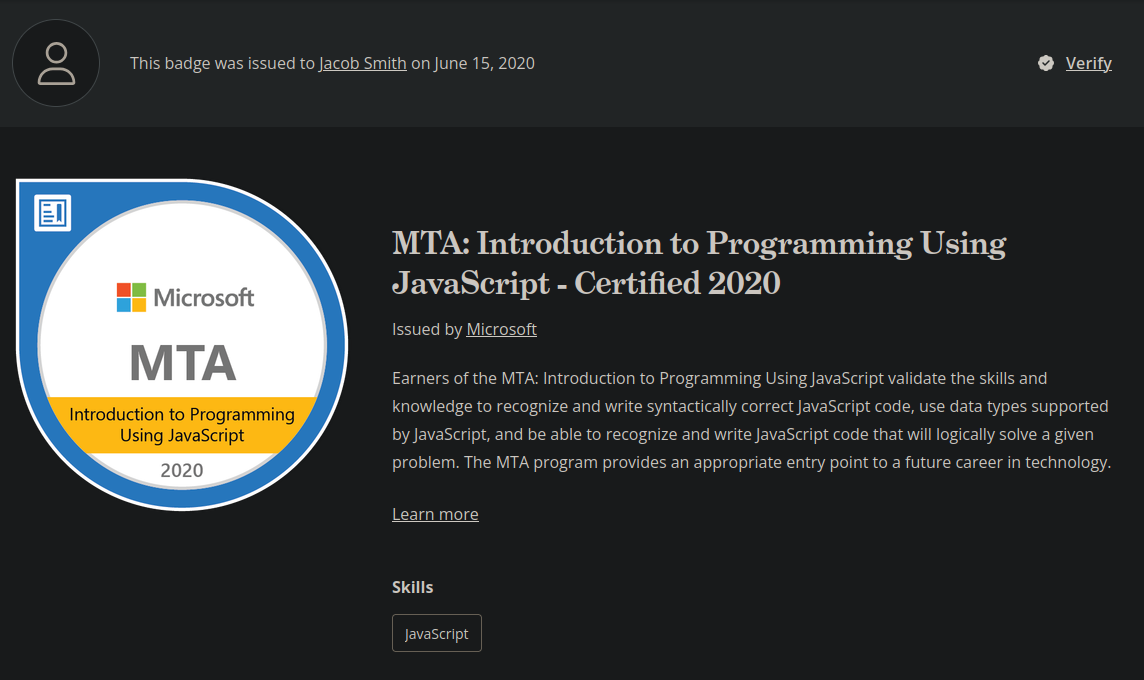
MTA: Intro to JS
Shows a fundamental understanding of writing and developing in Javascript
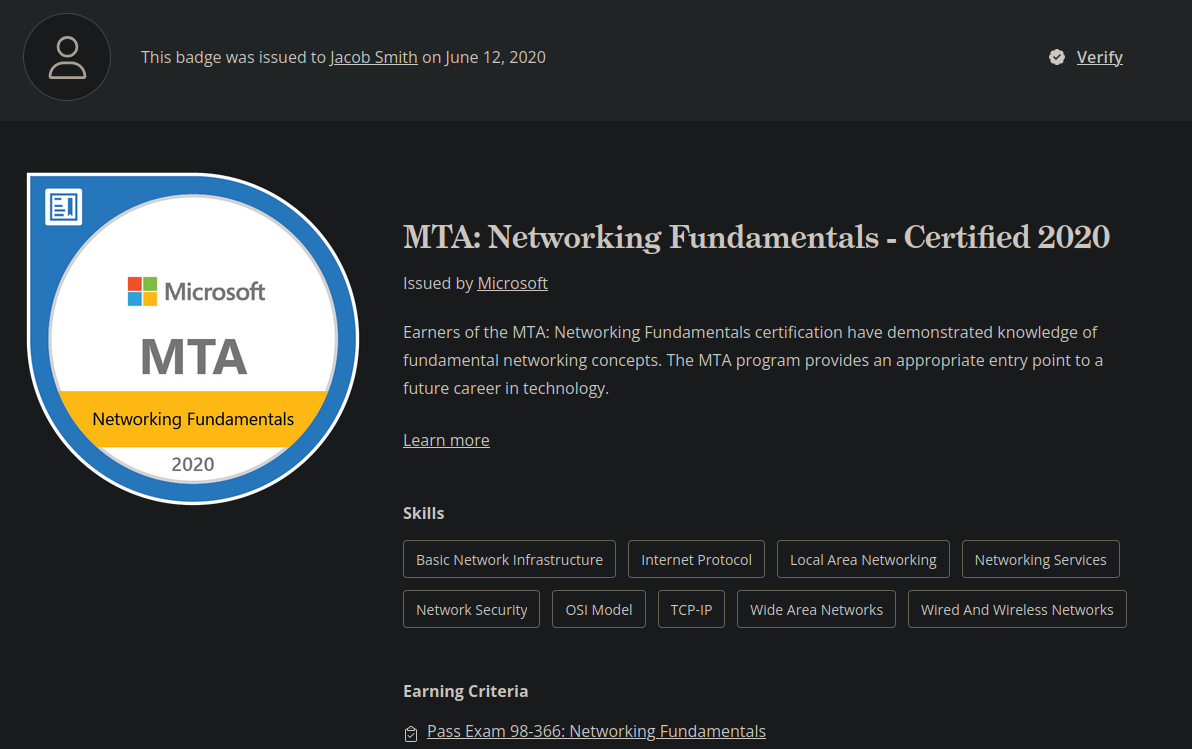
MTA: Network Fundamentals
Shows a fundamental understanding of networking concepts and management.
MTA: Windows OS Fundamentals (as of 2020)
Shows the fundamental understanding of Windows as of 2020 for performing configuration changes, upgrades, management, and more.